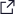“It takes experiencing disruption to critical operations for large organisations to take cybersecurity seriously and allocate adequate resources to ensuring cyber resilience.”
This damning analysis by Ross Brewer, vice president and managing director EMEA at cyber firm Graylog, sums up much of the zeitgeist around digital threats in the oil and gas industry until 2021.
In May that year, the US’ Colonial Pipeline was shut down by a ransomware attack – followed a month later by a $50m ransom demand by hackers who breached Saudi Aramco’s data systems.
This series of troubling events served as “a wake-up call to oil companies and governments, especially the White House”, according to David Bicknell, principal thematic analyst at GlobalData.
“Critical national infrastructure worldwide continues to be under threat, not least because of a more complex geopolitical world,” Bicknell tells Power Technology. “We live in challenging cybersecurity times.”
Early warning signs
Oil and gas conglomerates had their first warning nearly ten years prior.
Saudi Aramco was again the victim of a ransomware attack, which infected 35,000 computers and impeded daily operations.
“In response [to the 2012 Aramco hack], these large organisations have significantly tightened cybersecurity policies and procedures,” Brewer says. “In the last few years, the industry has begun implementing more rigorous measures and processes to thwart attacks and minimise vulnerability to their environment. For vendors this means going through extensive vetting as well as testing new systems, before allowing new installations.”
For Saudi Aramco, that meant signing an MoU with US operational technology firm Dragos to help secure its critical infrastructure and assets – but only after the second hack in 2021.
There is, however, “more to be done”, in Brewer’s words.
“The global petrochemical industry is uniquely positioned at the crossroads of activism and geopolitics, making it a prime target for diverse cyber threats,” says Brewer. “It is crucial for these organisations to adopt a proactive cybersecurity approach, with robust monitoring systems that detect and neutralise threats at their source.”
One in every ten organisations worldwide were hit by attempted ransomware attacks in 2023, surging 33% from the previous year, when one in every 13 organisations received ransomware attacks, according to Check Point Research.
A target on oil and gas firms’ backs
With cyberattacks on utilities rising by more than 200% in 2023, Bicknell’s assertation that “many of those attacks will be targeted at utilities companies” bears weight.
There is a geopolitical target on many oil and gas companies because of their connections to nation-states. Russia’s Gazprom, Chevron and Exxon in the US, Norway’s Equinor, Italy’s ENI and, most recently, Great British Energy in the UK.
Such conglomerates are massive money-spinners for their respective nations, and therefore a prime target for hacktivists looking to dent a geopolitical rival’s earnings, often through distributed denial of service (DDoS) attacks.
The seemingly constant rise in profits for oil and gas companies also means that more mainstream cybergangs know the rewards of a successful ransomware attack are lucrative.
“The majority of cyberattacks on the oil and gas industry stem from financial motives. Hackers will use spear phishing, ransomware or supply chain attacks to steal sensitive information and demand a ransom,” says Brewer. “This space is particularly lucrative for criminal groups because of the widespread disruption that can be caused by hindering the operations of multinational petrochemical companies.”
Bolstered by governmental backing, analysts expect oil and gas firms’ investment into the highest-rated cybersecurity systems to rise.
But avoiding complacency from top-to-bottom will be crucial in such a targetable and profitable industry, Brewer concludes: “Oil and gas companies need to double down on basic cyber hygiene practices and develop forensic capabilities to effectively identify suspicious activity across attack vectors.”